Part 1 – How Did We Get Here?
Two words…. Netscape Navigator.
Let me back up a bit and go back to the beginning. 1990!
Shortly after the earth cooled and life began, Sir Tim Berners-Lee just decided to invent the world wide web. This was approximately 1990 give or take any prior research and general acceptance of the idea. He also put together the first browser confusingly and yet inspirationally called “WorldWideWeb”.
Well now you know how that all started and why it’s called what it is. For those of you who were toddlers or perhaps not even born yet a world without the web sounds like a time when everything was in black and white, lit by open flame, the notion of evolution was exciting and new and tablets were made from stone.
Since then things have evolved. The browser which began as a simple visual interpretation of a “markup” language used to create a textual representation of visual elements is now a dangerously functional run-time environment potentially comparable to our host operating system, (eg. Linux, Windows, MacOS) more than you might expect. Developers may compare the browser to the Java Virtual Machine (JVM) or the Common Language Runtime (CLR) upon which many of newer desktop the applications you enjoy run.
The original language of the Browser was HTML ( Hyper Text Markup Language ). Waaaay back in 1995 I had a web development company. Back then, in order to be a web developer you had to know how to make static HTML pages and potentially, if you had mad website skills, have a handle on early versions Adobe Photoshop to make simple buttons and graphics using the new and game changing “bevel” and “drop shadow” filters which were rocking the graphics world at the time. In 1995 buttons just got real baby.
In the 90s the browser world was very different. There was no Chrome (there was no google for most of it), or Firefox or Safari. Early browsers like Lynx ( an actual text based browser kind of like Great Britain’s old teletext channel ) and NCSA Mosiac gave way to more commercially developed works like Netscape Navigator.
I was a big Netscape guy. It was next level. In 1995 however, windows bundled their first version of Internet Explorer into the much promoted Windows 95 and Netscape essentially threw it’s rattle out of the pram over that and engaged in a anti-competitive law suit that would eventually put them, if not out of business, very much onto the back foot (even though they were right). Netscape did however succeed in, and should be credited for, spawning two legendary foundation technologies. One of these was the Mozilla foundation which brought us Firefox.
The other was the original sin of the Browser, Javascript. It was originally called Mocha and then Livescript. Frankly because the language has sweet ‘F’ all to do with the language Java, probably should have been kept as one of those. Thanks to the Netscape marketing department wanting to ride on the Java popularity coattails we are stuck with Javascript (a.k.a. JS). For developers who like a bit of geek fact, Netscape were also the trailblazers for server side Javascript like, but not directly connected to, NodeJS. It’s fair to say that Netscape’s technological reign. although short lived, laid some serious groundwork for where we are now.
Browser Power
Why did I refer to Javascript as the original sin of the browser? It introduced some magic that changed our browsing experience in an fundamental way. No longer were web pages or web sites developed in a static brochure style using only basic hyper links (remember the “blink” tag) to load new content and generate interactivity. Javascript allowed for web developers to embed programming into the page itself and create, modify and react to the page. At first it was used for simpler things like form validation. It could make sure you entered an email address formatted correctly before allowing for the data to be submitted to the server. This made for a better user experience and for faster performance because now some of the decision making was taking place on the client side instead of shifting 100% of the burden to the server.
Of course Javascript would have been sincerely limited without it’s sister initiative called the DOM (Document Object Model). The DOM is essentially a programmatic map of the web page which is made available to the embedded language. In the early days both Microsoft and Netscape developed and largely fought over how this should look until the 2000s when it started to fall into a standard.
Fast forward slightly to around 2004 when DOM Level 3 was published, adding support for sexy new event handling among other super fun new features. It’s no surprise that software security guru Gary McGraw released his seminal book Software Security shortly afterwards in 2006. Web page and web sites were now being called web applications and things were changing fast. Faster than we potentially realised at the time.
Just so we all know what’s going on with this browser language and what it now enabled developers creating web applications to do:
JavaScript can add, change, and remove all of the HTML elements and attributes in the page.
JavaScript can change all of the CSS styles in the page.
JavaScript can react to all of the existing events in the page.
JavaScript can create new events within the page.
Essentially the language can rewrite everything on the page. It has total control and is was turned largely form based interactions into… well let’s say it… Facebook. Facebook and Google Mail are serious web applications. Also organisational tools like Trello, Wunderlist and Evernote are great examples of what is possible within the browser. A web application with dynamic content, real-time updates and interactivity between users.
Skipping forward to the present day (roughly 2018), going back 15 years, what a modern web application does, you would have expected to have to download and run something on your computer, now known as “the desktop”, like Microsoft Word or Excel. Even those desktop juggernauts are now available in a web hosted form leaving it seeming pretty strange when you have to actually download something. It fills me with dread these days and I generally assume that it’s some kind of malicious malware if a download is required (and so should you actually). Things have changed.
Let’s take a look at the modern Browser Power and what it can do to compromise our own security and what we should watch out for.
To reiterate the capabilities of a modern browser and the web applications we load into them
JavaScript can add, change, and remove all of the HTML elements and attributes in the page.
JavaScript can change all of the CSS styles in the page.
JavaScript can react to all of the existing events in the page.
JavaScript can create new events within the page.
We should also consider the change in application development from desktop to web based. There are some key differences in the trust model that we should acknowledge and take into consideration. With the legacy model where we download and run an application, we trusted the organisation (eg. Microsoft) and therefore the product. Once the product was installed and proven we trusted it to continuing being trustworthy because we hadn’t changed it. Additionally there were no shortage of virus checking software solutions like McAfee and Comodo ready to jump on anything that looked out of sorts.
In those days our big threat was when Microsoft added scripting to their suite of Office products and so began the malicious Word document era which ran took a trust application and used it against us to run all sorts of wonderful malicious code and still does. Check out the ransomware podcast for details on that. Yes people still get fooled into opening dangerous Word or Excel documents AND allow for the scripts to run.
Getting back to the trend towards web applications, if we consider the trust model, we’ve be taught to trust something we’ve already used successfully. What we need to acknowledge is that each time we return to something like Facebook or Netflix, it’s highly unlikely we’re actually running the same application in our browser even though it make roughly or exactly look the same. Take a look at Netflix for a highly advanced example of how development really works today. They are the benchmark continuous integration and deployment boasting an approximate 16 minutes between a developing changing the code and it being deployed globally. https://medium.com/netflix-techblog/how-we-build-code-at-netflix-c5d9bd727f15
We are heavily reliant on developers making changes we can trust in real time and having processes to safe guard the security of the applications that we are running in our browsers to ensure that the trust we are giving them, often without proper or perhaps any consideration is valid.
In the case of major players like Facebook, LinkedIn and Netflix, security is paramount and a secure development culture, tools and processes are all part of the environment but that isn’t necessarily the same for every organisation, in particular smaller companies who haven’t the expertise or knowledge of to even really know what they are missing. The demand for web applications is turning many companies who previously thought of themselves as a courier company, a banking company, a hardware manufacturer, a hotel or restaurant, a book store, an… insert company here… into a software company.
In terms of Web Applications there are organisations like the Open Web Application Security Project (or OWASP for short) (and yes their logo is a wasp) who are regularly assessing the top 10 security problems for such applications and providing as much assistance as possible to ensure developers and organisations are educated and prepared so the world of application security is, for the most part (and by that we don’t see major applications we deal with daily getting hacked) under relative control.
The browser itself is somewhat different. The attack surface is continually changing and growing. To be transparent, the phrase attack surface is security geek speak for looking at an application and looking at how complex the outward facing interface is. Kind of like looking at your house and really checking for every way an intruder could get in. That’s the attack surface.
The house really works as an analogy. Problems with security can be the architecture itself (eg, poor design or poor materials or outdated foundations), extensions (did you really need that conservatory?), or bad builders (you get what you pay for). The browser is no different.
Part 2 – Exploiting the Attack Surface
In this section we talk about known exploits in the browser from how file types have tricked the browser, and the OS, into giving away credentials to hacked browser extensions, to crypto mining to the potential for trusted websites to undermine our confidence and off up malvertising and lead us off the safe path. While we discuss a few examples, we are only scraping the surface of what is possible.
In short… it’s a quick, learn from the mistakes of the past, cautionary tale about browsing the internet in the modern (2018) world. I would be worried that I was dating this post but, as it’s a tech blog (podcast), it’ll be dated faster than you can say Betamax.
GO BOSKO!
Just last year researcher Bosko Stankovic found a way to exploit an older and essentially outdated file extension called .scf. Ever heard of that file extension? Me neither. It’s like an early predecessor of the .lnk shortcut link. If you’re a security savvy individual you may recall that the Stuxnet breach which attempted to destroy Iran’s nuclear program. This was done through a powerful malware which got into the system via a malicious .lnk file. Yes a malicious shortcut file. Crazy isn’t it. Stankovic found that because Chrome will download known safe file types without asking it will download a .scf file. You may think that you still need to run malicious files right? What’s even more exciting about this is that… well you know when you visit a folder in explorer and it creates cool little icons for each file? A .scf file can specify the location of that Icon which means without executing anything explorer will go to the location to find it and that location doesn’t have to be on your computer. It can be remote. If the remote computer pretends to be an SMB server, the Server Message Block (SMB) protocol works will initiate the NTLM (NT Lan Manager) challenge/response authentication mechanism. Stankovic proved that this will allow a remote agent to capture the windows credentials which could be used for all sorts of nasty ends.
THAT NEW EXTENSION!
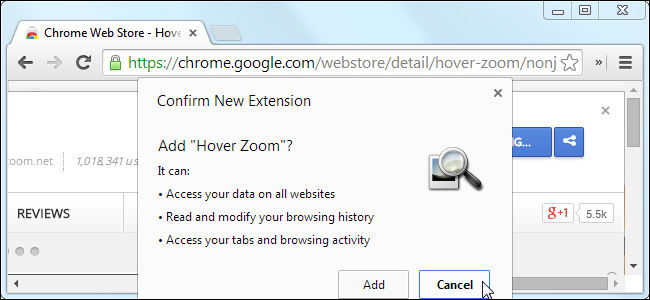
Lets consider for a moment browser extensions. Do you use any? In Firefox I used to have one called DownloadThemAll. In Chrome I have a few like Adobe Acrobat and Buffer (social media). Other popular extensions are Pinterest, Cisco Webex, Evernote Clipper. You might have Chrome extensions and not really realise it. It’s a worth a check. In Chrome it’s under the vertical (…) on the far right. Then navigate to “more tools” and “extensions”. Make sure you recognise everything there and be sure when you add an extension that you are happy with the privileges you give it. It can even be worth removing and re-adding an extension to see what it asks for if you’ve had it for a while and can’t remember what you agreed to upon installing it.
Chrome extensions are largely written in our old friend Javascript. Remember that list of powers that Javascript has?
For a recent example of just what’s possible, in the month of February 2018, a company called TextHelp had their plugin (plugin = extension) called BrowseAloud hacked such that anyone using it (more than 5,000 websites) ended up running some malware/crypto-jacking software known as Coinhive. Coinhive takes advantage of the processing power of a your computer or device to mine the cryptocurrency Monero. Check out our 2 part podcast on Blockchain, Security and the Cryptocurrency Boom!
Read more here https://www.theguardian.com/technology/2018/feb/11/government-websites-hit-by-cryptocurrency-mining-malware
What was interesting about that effort to mine currencies on behalf of the bad guys is that, technically you don’t really have to hack anything to make that happen. Recently a Starbucks in Buenos Aires, Argentina was using their “Wait for a few moments while we connect you” page to mine cryptocurrency on the laptops of coffee enthusiasts who logged into their local wifi. It wasn’t clear if this was Starbucks or the Wifi provider. We didn’t see anything mentioned in the press about anyone being “hacked” so we will leave that one to speculation.
Consider also that anyone can write an extension for Chrome or Firefox and make it available. It’s worth noting that a bit more like Apple, Chrome only downloads extensions from its own store which could be considered much safer. However… very much like some of the applications available in the Google Play store for Android phones aren’t actually safe or well intended, the same goes for browser extensions.
While writing a new malicious extension is possible, in order to get it into the store could reveal some much desired anonymity. What seems to be a more typical route for extension hackers is to use that old classic, phishing emails, to try to compromise the developer group working on the extension or plugin to gain access to their Chrome Web Store. If they can gain those credentials, they can simply just swap out a known trusted (there’s that word again) extension for a similar but different version.
Just in 2017 these extensions were compromised.
Chrometana
Infinity New Tab
CopyFish
Web Paint
Social Fixer
TouchVPN
Betternet VPN
https://thehackernews.com/2017/08/chrome-extension-hacking.html
I find it of particular ironic interest when the bad guys take what is meant to be a security or privacy aid like VPN and use that against us. I’m referring more to Betternet than TouchVPN as TouchVPN is more marketed at trying to get out of country Netflix shows (it works… I tested it… purely research of course).
In the case of many of the compromised extensions above, the result was an interception of traffic to present malicious advertising in order to push viewers to malicious or spoofed websites which may attempt to steal credentials or download malware.
What’s interesting about so many of the plugin breaches is that it could have done so much more. If you think about what you can do with the power of distributed computing, which is all the rage with blockchain technologies at the moment. Blockchain blockchain blockchain… better get just one more in there…. blockchain. It is quite straight forward to use a compromised extension to inject a small section of Javascript code to orchestrate a distributed denial of service (DDoS) attack against a specified target web site using the browser power of 1000s of unknowing individuals. Early examples of distributed tech would be SETI. You know there was always a guy at your work helping out the intelligent life space cause.
Something I mentioned in our podcast on Passwords was how it was possible to intercept user names and passwords held by the browsers password manager by presenting an invisible login screen while a user was already logged into a known domain.
There have been several extensions and web applications to do with cryptocurrencies which have been compromised to reroute cryptocurrency transactions via your online “hot” wallet to the bad guys wallet instead of your intended destination. A very recent one being the Black Wallet Stellar Lumen wallet application which had some Javascript injected to check and remove all your crypto.
One unexpected path to, yet again, getting a bit of unwanted javascript code running on your computer is to use something called a DOM XSS. I mentioned the DOM earlier as being this map of a web page that allows Javascript access to the whole kit and kaboodle.
As an example of DOM XSS… have you ever copied and pasted a URL you wanted a friend to see into an email and thought, “holy shittake mushrooms that’s a huge URL!”. Typically URLs have a ton of extra tokens and cookies and other crap that make it hard to understand. Sometimes there are simple parameters on the URL line like look a bit like ?language=French. That’s a good example because lots of sites are language specific.
Here’s a link to a random Brewdog link that showed up while I was on Facebook. We so used to seeing links like that we might not notice a malicious version.
https://www.brewdog.com/equityforpunks?utm_source=facebook&utm_medium=cpc&utm_campaign=UK_EFPV_Remarketing_AllDevices
If the page you’re on doesn’t check a parameter before using it (this is called sanitising input by the way) you could change the word french to be some javascript that … mines crypto currency or scans the page for personal information or… the list goes on. I would hope we don’t have to worry too much about that as most modern sites are designed to avoid this vulnerability by sanitising inputs OR just avoiding URLS like this completely. I guarantee some older sites though are definitely not. It can be a fun afternoon surfing around trying to find some. https://www.owasp.org/index.php/DOM_Based_XSS
A final chink in the browser armour (if you imagine armour made of lettuce or origami birds) is advertising. Or malvertising as it’s come to be known. Even simpler non web-app sites are allowing for remote advertising servers to inject advertising code which displays advertising onto their page. For high-profile and reputable websites, there is an opportunity to bypass firewalls and undermine even the most cautious user like yours truly.
In 2015, malvertising was responsible for the deployment of the CryptoWall Ransomware which took $1 million of ransom money by infecting over 600,000 computers.
Malvertising can inject code to exploit the user locally (like crypto-miners) or something to abuse the trust of the host site and lure you to a too-good-to-be-true offer on a remote malicious site.
BUT WAIT, THERE’S MORE!
Clickjacking
This is where the javascript presents a whole different page over top of the page you’re actually at. You might think you are clicking on one thing but actually the click is taking effect on something you can’t even see. Pretty amazing isn’t it! And scary. It’s like that old trick you see in movies where they drop one paper over another and make you sign up to something you didn’t want to.
There is a sub-set of that called Like Jacking. A new one in the world of social media. This one can trick in you into Liking something on Facebook! How dare they! Surely you value your Likes as much as I do.
Other examples of social media type things Javascript can make you do without knowing would be…
Tricking users into enabling their webcam and microphone through Flash (though this has been fixed since originally reported)
Making users follow someone on Twitter
Sharing or liking links on Facebook
Getting likes on Facebook fan page or +1 on Google+
Clicking Google AdSense ads to generate pay-per-click revenue
Playing YouTube videos to gain views
Following someone on Facebook
WHAT CAN WE DO?
In summary… When you’re using coded web applications, browser extensions or even visiting a simpler websites which are allowing for remote advertising servers to inject content, there is an opportunity for malicious code to take advantage of your resources, your private information, and your trust.
When you think about it… what I just said covers about 99.9% of the websites you visit and probably a reasonable portion of the time you spend on your computer or device (I haven’t even gotten started on Android devices as that is a whole other podcast).
The best thing you can do, and I say this a lot, is keep all of your tech up to date. OS, phones, browsers, home routers, software of any kind. Using out of date browsers is like using windows XP. Old browsers have old vulnerabilities. It’s hard enough to protect yourself in 2018 without acting like it’s 2009.
Also… a close 2nd is to make sure, if you can, that you are browsing the Internet as a least-privilege user account (i.e. without administrator privileges). If you’re on a work computer or a Mac, this is probably already the case. This limits the ability of a security exploit in a web browser from compromising the whole operating system.
In the case of the crypto-jacking, it’s actually pretty harmless. While you’re making money for somebody else, there hasn’t been many cases of it having an alternative agenda. Evidence of live crypto-jacking could be found by hitting Ctrl Alt Del on a PC, launching the Task Manager. Sort the processes by Memory or CPU usage and there will likely be several tabs from your favourite browser in the top 25 for memory usage. It’s worth closing each browser tab one by one to find the offender and just don’t use that site again. It’s that easy.
In terms of what can WE do… it’s limited other than be aware. There’s is far more onus on developers of these trust applications and extensions to ensure there are secure from design to deployment and far too often, they haven’t either the expertise or motivation.
Further to the what can we do… I’ll step into irony corner for a moment and mention that there are adblocker browser extensions. Yes I realise I’m recommending an extension. Things like AdBlock Plus can help with Browser security. It’ll help with the malvertising but introduce a new browser plugin and a new vector of trust. At least they have a lot more to lose if their plugin is compromised somehow. Other options exist like https://www.qualys.com/free-tools-trials/browsercheck/personal/
Finally I feel I should mention Privacy mode in the browser. You would be mistaken if you think this means Security mode.
Privacy mode, also known as “I don’t want my partner to know about my porn” Mode keeps your recently history non-persistent but doesn’t protect from the things we’ve discussed in this article. We’ll talk more about what Private mode actually means in a podcast on privacy and keeping your data safe.